Configuration of Keycloak for PAT exchange
Introduction
The configuration below is required when using the functionality of exchanging Personal Access Tokens (PAT) for access tokens, for example, when using H2O Drive.
When user is authenticated via Feature Store personal access token, exchange between this PAT and platform access token is required in case interacting with cloud components (Drive/GTPe).
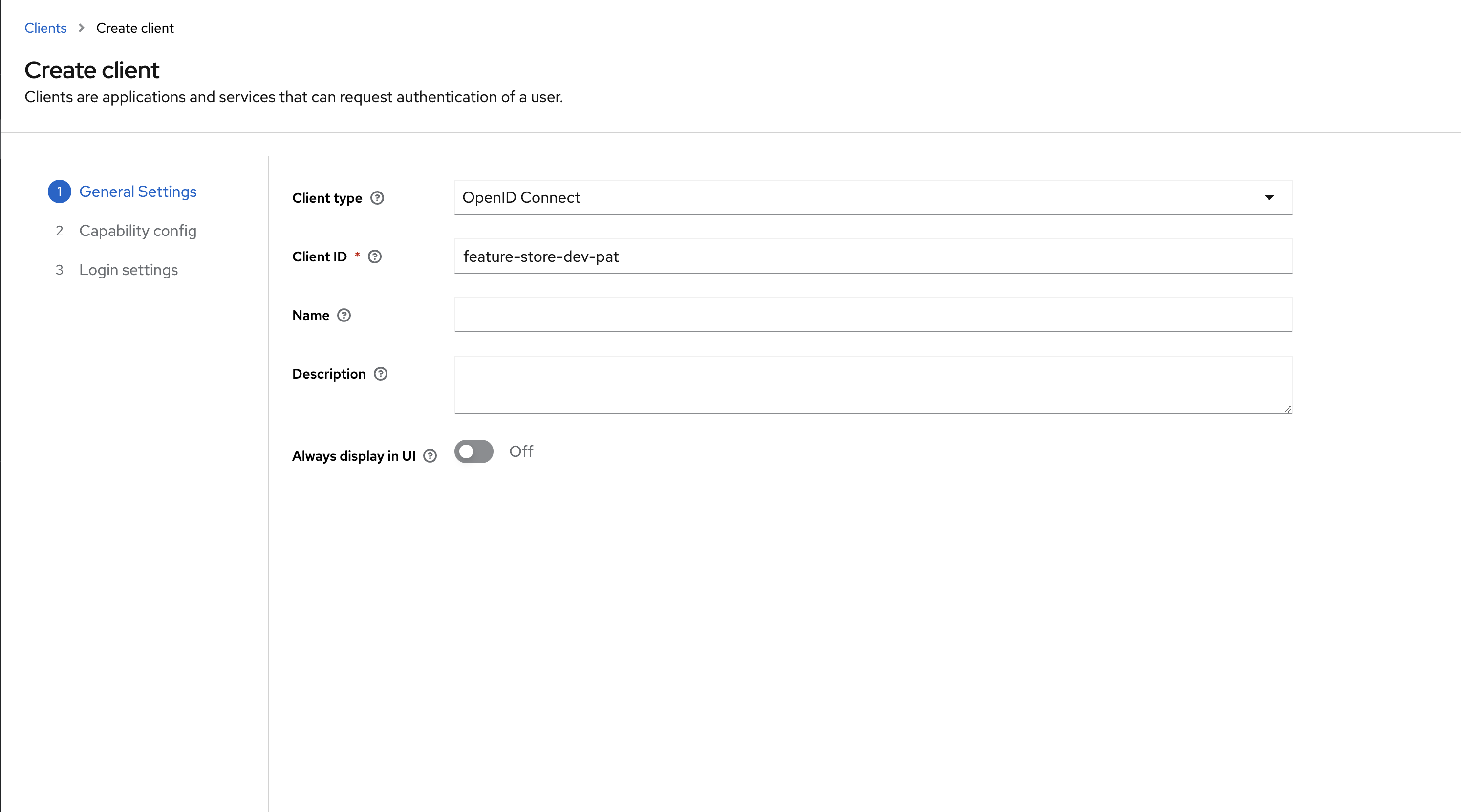
Register new client in the realm
- Select realm from drop-down
- Click Clients on the left panel and click Create client
- Select OpenID Connect in Client type
- Provide Client ID for example feature-store-pat
- Provide Name for example feature-store-pat
- Click Next
- Select Client authentication
- Select Standard flow , Direct access grants, Service accounts roles
- Click Next
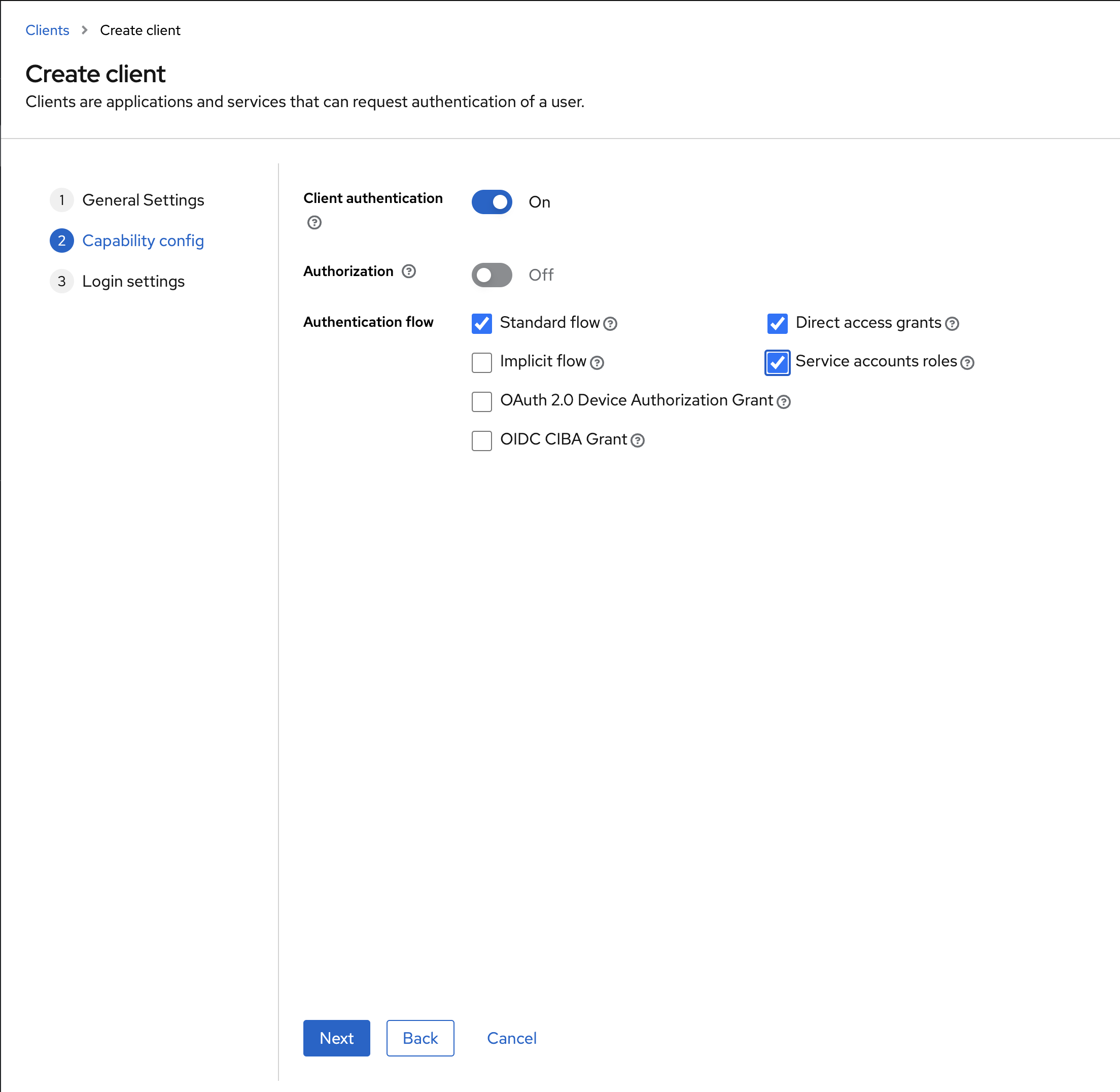
- Select Client authentication
- Select Standard flow , Direct access grants, Service accounts roles
- Click Next
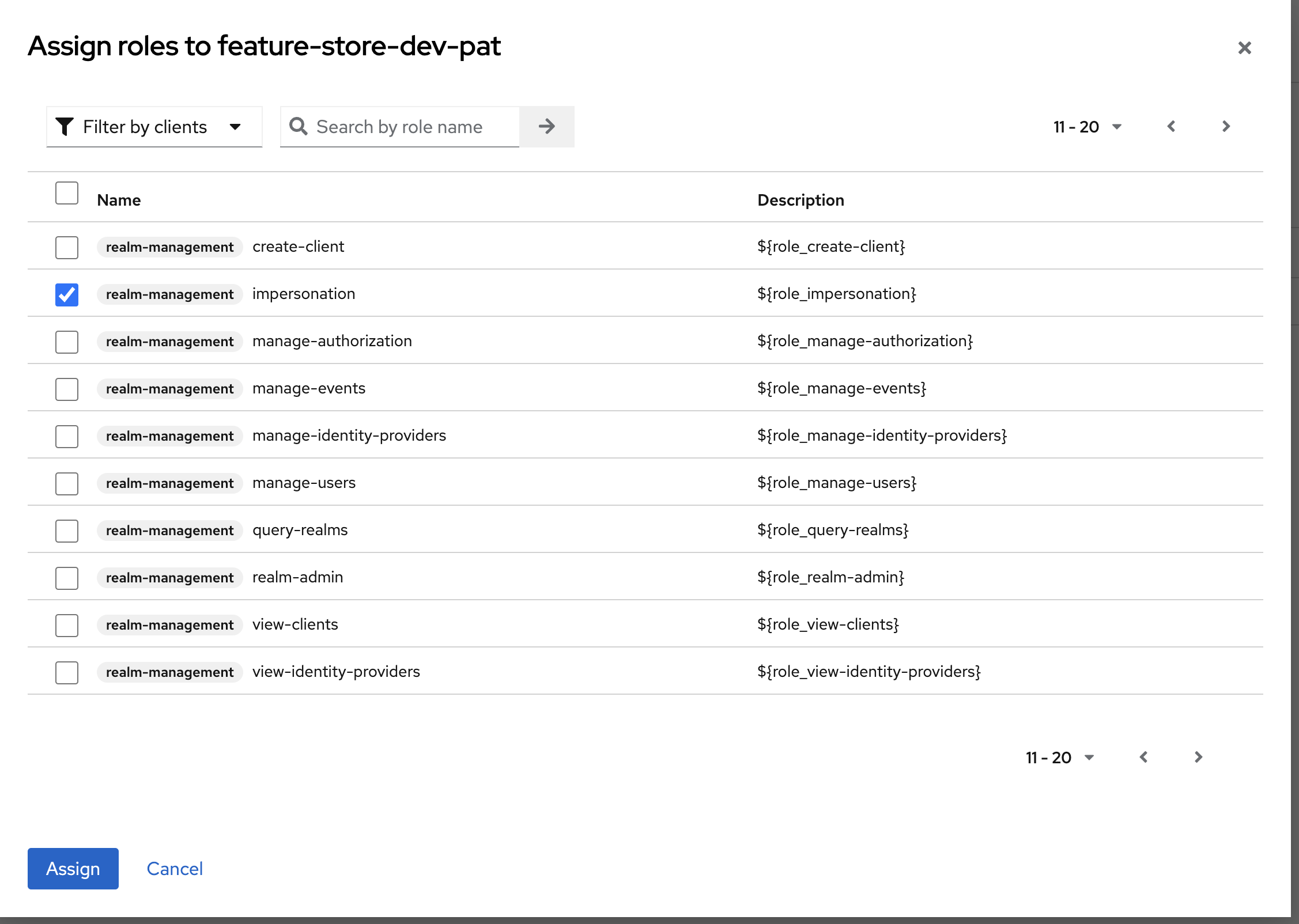
After creating the client, click on tab Service accounts roles and assing role.
- Select impersonation role
Deployment
Please start keycloak with parameter: -Dkc.features=token-exchange or KC_FEATURES=token-exchange
Feedback
- Submit and view feedback for this page
- Send feedback about H2O Feature Store to cloud-feedback@h2o.ai